Recent stories about Active Directory
Continue Reading This Article
Enjoy this article as well as all of our content, including E-Guides, news, tips and more.
Active Directory is designed especially for distributed networking environments. Active Directory was new to Windows 2000 Server and further enhanced for Windows Server 2003, making it an even more important part of the operating system.
Working with Microsoft Active Directory can be complicated and confusing if you aren't prepared, but with the right guidance any admin can learn to make AD work for them. SearchWindowsServer.com's Active Directory Learning Guide will bring you up to speed quickly on this important Windows technology and help ease the AD fear factor. This comprehensive tutorial provides the information every administrator should know, from the basics of Active Directory to tips and explanations regarding DNS, replication, security, migration planning and more.
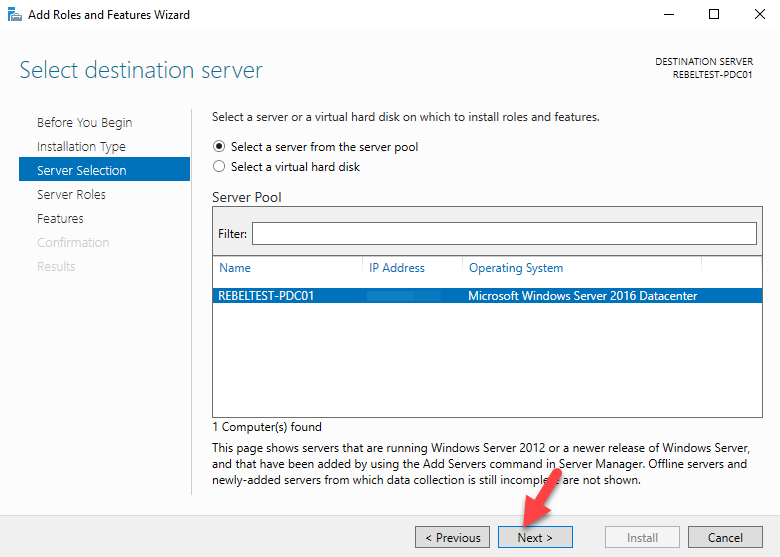
- Sign in to the Windows Server VM. In the previous tutorial, a Windows Server VM was created and joined to the Azure AD DS managed domain. Let's use that VM to install the management tools. If needed, follow the steps in the tutorial to create and join a Windows Server VM to a managed domain.
- There are interesting new features now made available in Windows Server 2016 such as time based group membership, privileged access management, and others. Most will be covered in future posts. This post will detail how to install active directory on Windows Server 2016.
- In this chapter, we will see how to Install Active Directory in Windows Server 2012 R2. Many of us who have worked with the previous version run DCPROMO.EXE to install it, but in the 2012 version, it is recommended by Microsoft not to use it anymore. To continue with Installation follow the steps.
- Tutorial: Join a Windows Server virtual machine to a managed domain.; 12 minutes to read; In this article. Azure Active Directory Domain Services (Azure AD DS) provides managed domain services such as domain join, group policy, LDAP, Kerberos/NTLM authentication that is fully compatible with Windows Server Active Directory.
Table of contents:
- Start here: a guide to Active Directory
- Active Directory basics
- DNS and Active Directory
- Active Directory replication
- Security and Active Directory
- Active Directory planning and design
- Microsoft Group Policy Tutorial
- Changes to Active Directory
- More Active Directory topics
You can follow SearchWindowsServer.com on Twitter @WindowsTT.
Active Directory basics
In this section, learn about the basics of Active Directory and the benefits of Active Directory implementation. Find information on Active Directory forests, domains, organizational units and sites, as well as the basics of LDAP (Lightweight Directory Access Protocol) and Group Policy. After that, move on to the next section of our Active Directory Learning Guide, which focuses on the Domain Name System (DNS).
The basics of Active Directory
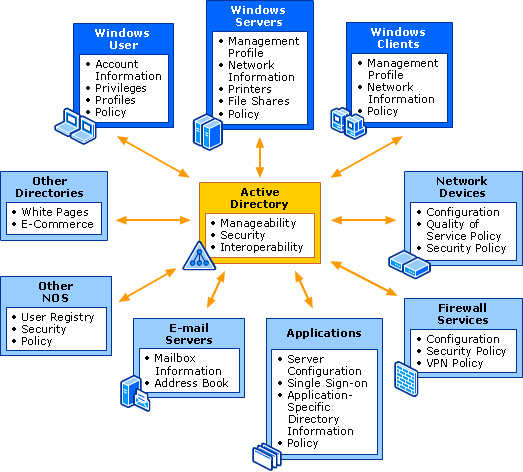
What is Active Directory? Active Directory is Microsoft's trademarked directory service, an integral part of the Windows architecture. Like other directory services, such as Novell Directory Services (NDS), Active Directory is a centralized and standardized system that automates network management of user data, security and distributed resources and enables interoperation with other directories. Active Directory is designed especially for distributed networking environments.
Active Directory was new to Windows 2000 Server and further enhanced for Windows Server 2003, making it an even more important part of the operating system. Windows Server 2003 Active Directory provides a single reference, called a directory service, to all the objects in a network, including users, groups, computers, printers, policies and permissions.
For a user or an administrator, Active Directory provides a single hierarchical view from which to access and manage all of the network's resources.
Why implement Active Directory?
There are many reasons to implement Active Directory. First and foremost, Microsoft Active Directory is generally considered to be a significant improvement over Windows NT Server 4.0 domains or even standalone server networks. Active Directory has a centralized administration mechanism over the entire network. It also provides for redundancy and fault tolerance when two or more domain controllers are deployed within a domain.
Active Directory automatically manages the communications between domain controllers to ensure the network remains viable. Users can access all resources on the network for which they are authorized through a single sign-on. All resources in the network are protected by a robust security mechanism that verifies the identity of users and the authorizations of resources on each access.
Even with Active Directory's improved security and control over the network, most of its features are invisible to end users; therefore, migrating users to an Active Directory network will require little re-training. Active Directory offers a means of easily promoting and demoting domain controllers and member servers. Systems can be managed and secured via Group Policies. It is a flexible hierarchical organizational model that allows for easy management and detailed specific delegation of administrative responsibilities. Perhaps most importantly, however, is that Active Directory is capable of managing millions of objects within a single domain.
Basic divisions of Active Directory
Active Directory networks are organized using four types of divisions or container structures. These four divisions are forests, domains, organizational units and sites.
- Forests: The collection of every object, its attributes and attribute syntax in the Active Directory.
- Domain: A collection of computers that share a common set of policies, a name and a database of their members.
- Organizational units: Containers in which domains can be grouped. They create a hierarchy for the domain and create the structure of the Active Directory's company in geographical or organizational terms.
- Sites: Physical groupings independent of the domain and OU structure. Sites distinguish between locations connected by low- and high-speed connections and are defined by one or more IP subnets.
Forests are not limited in geography or network topology. A single forest can contain numerous domains, each sharing a common schema. Domain members of the same forest need not even have a dedicated LAN or WAN connection between them. A single network can also be the home of multiple independent forests. In general, a single forest should be used for each corporate entity. However, additional forests may be desired for testing and research purposes outside of the production forest.
Domains serve as containers for security policies and administrative assignments. All objects within a domain are subject to domain-wide Group Policies by default. Likewise, any domain administrator can manage all objects within a domain. Furthermore, each domain has its own unique accounts database. Thus, authentication is on a domain basis. Once a user account is authenticated to a domain, that user account has access to resources within that domain.
Active Directory requires one or more domains in which to operate. As mentioned before, an Active Directory domain is a collection of computers that share a common set of policies, a name and a database of their members. A domain must have one or more servers that serve as domain controllers (DCs) and store the database, maintain the policies and provide the authentication of domain logons.
With Windows NT, primary domain controller (PDC) and backup domain controller (BDC) were roles that could be assigned to a server in a network of computers that used a Windows operating system. Windows used the idea of a domain to manage access to a set of network resources (applications, printers and so forth) for a group of users. The user need only to log in to the domain to gain access to the resources, which may be located on a number of different servers in the network.
One server, known as the primary domain controller, managed the master user database for the domain. One or more other servers were designated as backup domain controllers. The primary domain controller periodically sent copies of the database to the backup domain controllers. A backup domain controller could step in as primary domain controller if the PDC server failed and could also help balance the workload if the network was busy enough.
With Windows 2000 Server, while domain controllers were retained, the PDC and BDC server roles were basically replaced by Active Directory. It is no longer necessary to create separate domains to divide administrative privileges. Within Active Directory, it is possible to delegate administrative privileges based on organizational units. Domains are no longer restricted by a 40,000-user limit. Active Directory domains can manage millions of objects. As there are no longer PDCs and BDCs, Active Directory uses multi-master replication and all domain controllers are peers.
Organizational units are much more flexible and easier overall to manage than domains. OUs grant you nearly infinite flexibility as you can move them, delete them and create new OUs as needed. However, domains are much more rigid in their existence. Domains can be deleted and new ones created, but this process is more disruptive of an environment than is the case with OUs and should be avoided whenever possible.
By definition, sites are collections of IP subnets that have fast and reliable communication links between all hosts. Another way of putting this is a site contains LAN connections, but not WAN connections, with the general understanding that WAN connections are significantly slower and less reliable than LAN connections. By using sites, you can control and reduce the amount of traffic that flows over your slower WAN links. This can result in more efficient traffic flow for productivity tasks. It can also keep WAN link costs down for pay-by-the-bit services.
The Infrastructure Master and Global Catalog
Among the other key components within Active Directory is the Infrastructure Master. The Infrastructure Master (IM) is a domain-wide FSMO (Flexible Single Master of Operations) role responsible for an unattended process that 'fixes-up' stale references, known as phantoms, within the Active Directory database.
Phantoms are created on DCs that require a database cross-reference between an object within their own database and an object from another domain within the forest. This occurs, for example, when you add a user from one domain to a group within another domain in the same forest. Phantoms are deemed stale when they no longer contain up-to-date data, which occurs because of changes that have been made to the foreign object the phantom represents, e.g., when the target object is renamed, moved, migrated between domains or deleted. The Infrastructure Master is exclusively responsible for locating and fixing stale phantoms. Any changes introduced as a result of the 'fix-up' process must then be replicated to all remaining DCs within the domain.
The Infrastructure Master is sometimes confused with the Global Catalog (GC), which maintains a partial, read-only copy of every domain in a forest and is used for universal group storage and logon processing, among other things. Since GCs store a partial copy of all objects within the forest, they are able to create cross-domain references without the need for phantoms.
Active Directory and LDAP
Microsoft includes LDAP (Lightweight Directory Access Protocol) as part of Active Directory. LDAP is a software protocol for enabling anyone to locate organizations, individuals and other resources such as files and devices in a network, whether on the public Internet or on a corporate intranet.
In a network, a directory tells you where in the network something is located. On TCP/IP networks (including the Internet), the domain name system (DNS) is the directory system used to relate the domain name to a specific network address (a unique location on the network). However, you may not know the domain name. LDAP allows you to search for individuals without knowing where they're located (although additional information will help with the search).
An LDAP directory is organized in a simple 'tree' hierarchy consisting of the following levels:
- The root directory (the starting place or the source of the tree), which branches out to
- Countries, each of which branches out to
- Organizations, which branch out to
- Organizational units (divisions, departments and so forth), which branch out to (include an entry for)
- Individuals (which include people, files and shared resources, such as printers)
An LDAP directory can be distributed among many servers. Each server can have a replicated version of the total directory that is synchronized periodically.
It is important for every administrator to have an understanding of what LDAP is when searching for information in Active Directory and to be able to create LDAP queries is especially useful when looking for information stored in your Active Directory database. For this reason, many admins go to great lengths to master the LDAP search filter.
Group Policy management and Active Directory
It's difficult to discuss Active Directory without mentioning Group Policy. Admins can use Group Policies in Microsoft Active Directory to define settings for users and computers throughout a network. These setting are configured and stored in what are called Group Policy Objects (GPOs), which are then associated with Active Directory objects, including domains and sites. It is the primary mechanism for applying changes to computers and users throughout a Windows environment.
Through Group Policy management, administrators can globally configure desktop settings on user computers, restrict/allow access to certain files and folders within a network and more.
It is important to understand how GPOs are used and applied. Group Policy Objects are applied in the following order: Local machine policies are applied first, followed by site policies, followed by domain policies, followed by policies applied to individual organizational units. A user or computer object can only belong to a single site and a single domain at any one time, so they will receive only GPOs that are linked to that site or domain.
GPOs are split into two distinct parts: the Group Policy Template (GPT) and the Group Policy Container (GPC). The Group Policy Template is responsible for storing the specific settings created within the GPO and is essential to its success. It stores these settings in a large structure of folders and files. In order for the settings to apply successfully to all user and computer objects, the GPT must be replicated to all domain controllers within the domain.
The Group Policy Container is the portion of a GPO stored in Active Directory that resides on each domain controller in the domain. The GPC is responsible for keeping references to Client Side Extensions (CSEs), the path to the GPT, paths to software installation packages, and other referential aspects of the GPO. The GPC does not contain a wealth of information related to its corresponding GPO, but it is essential to the functionality of Group Policy. When software installation policies are configured, the GPC helps keep the links associated within the GPO. The GPC also keeps other relational links and paths stored within the object attributes. Knowing the structure of the GPC and how to access the hidden information stored in the attributes will pay off when you need to track down an issue related to Group Policy.
For Windows Server 2003, Microsoft released a Group Policy management solution as a means of unifying management of Group Policy in the form of a snap-in known as the Group Policy Management Console (GPMC). The GPMC provides a GPO-focused management interface, thus making the administration, management and location of GPOs much simpler. Through GPMC you can create new GPOs, modify and edit GPOs, cut/copy/paste GPOs, back up GPOs and perform Resultant Set of Policy modeling.
Table of contents:
Then you can reset Windows 7 forgotten password directly on login screen after you find Windows 7 login password is incorrect.Insert password reset disk into Windows 7 computer, click the link Reset password and follow Password Reset Wizard to do. Windows 7 password turn off.
- Start here: a guide to Active Directory
- Active Directory basics
- DNS and Active Directory
- Active Directory replication
- Security and Active Directory
- Active Directory planning and design
- Microsoft Group Policy Tutorial
- Changes to Active Directory
- More Active Directory topics
Dig Deeper on Windows systems and network management
Group Policy
Windows Management Instrumentation (WMI)
How does Azure Update Management handle integration?
How a bastion forest limits exposure of admin privileges
Microsoft puts a new face on remote server management
Microsoft's VS Code embrace prompts PowerShell editor debate
Microsoft Azure Stack tweaks causing delays, IT pros still hopeful
With June Patch Tuesday, users need a fix for the fix
Group Policy
Windows Management Instrumentation (WMI)
How does Azure Update Management handle integration?
How a bastion forest limits exposure of admin privileges
How to use Azure Active Directory differently than classic AD
Do Active Directory functional levels still matter?
Can I use third-party tools to back up Active Directory?
What's new in Azure Active Directory Connect?
Windows Management Instrumentation (WMI)
Monitor Active Directory replication via PowerShell
Manage Linux servers with a Windows admin's toolkit
Use PowerShell for help with DNS server management
What are the guidelines for a better Active Directory backup?
Can I restore Active Directory to different hardware?
How to plan an Active Directory backup and restoration
Solving data consistency problems from Active Directory tombstones
- What’s Next in Digital Workspaces: 3 Improvements to Look for in 2019–Citrix
- A New Security Strategy that Protects the Organization When Work Is Happening ..–Citrix
- End-User Service Delivery: Why IT Must Move Up the Stack to Deliver Real Value–Citrix
- How to manage Group Policy Objects for Windows Vista– SearchWindowsServer
- The principles of Active Directory infrastructure ..– SearchWindowsServer
- Group Policies' order of application– SearchWindowsServer
You may have been following our series of blog posts on Active Directory basics and best practices that all kinds of IT specialists, from beginners to experienced IT administrators, found useful and insightful.
Today, we compiled a list of all these blog posts so you can easily find the Active Directory topic you are interested in.
This tutorial is a perfect tool to learn Active Directory step-by-step. Now, you can dive deep into Active Directory structure, services, and components, chapter by chapter, and find answers to some of the most frequently asked questions about Active Directory regarding domain controllers, forests, FSMO roles, DNS and trusts, Group Policy, replication, auditing, and much more.
Get the most out of this content by easily switching from one chapter to another.
Table of contents:
If you want to get all the chapters at once, we’ve got you covered – the AD series has been combined into one PDF document available for free download.
Active Directory Tutorial Pdf
What sources – blogs, forums etc – do you use to learn more about Active Directory? Please let us know in the comments to this post.